Dynamic HoneyPot Environment
My personal Honeypot Project is an initiative driven by a desire to gain practical, firsthand insights into the ever-evolving realm of cybersecurity threats. At its heart, this project involves a specially configured system deployed on a cloud server running the Ubuntu Live Server operating system, designed expressly to act as an intentional decoy. The core idea is to present what appears to be a vulnerable or appealing target to attract the attention of automated scanners, botnets, and opportunistic attackers traversing the internet. The primary engine driving this decoy environment is T-Pot, a comprehensive multi-honeypot platform that simplifies the emulation of various services commonly targeted by malicious actors. By setting up this controlled and isolated environment, the project aims to passively observe and meticulously log all interactions initiated by external entities. The ultimate goal is to collect and analyze real-time data on intrusion attempts, study the tactics, techniques, and procedures (TTPs) employed by attackers, and identify current trends in attack vectors. This gathered intelligence is invaluable, offering a tangible understanding of threats that goes beyond theoretical knowledge and directly contributes to enhancing awareness and informing the development of more effective defensive cybersecurity strategies. This project serves as both a powerful learning tool and a window into the day-to-day activities occurring on the front lines of cyber defense.


Introduction
Dynamic Environment
The impetus for establishing this honeypot project was a drive to gain practical, firsthand experience with the cyber threats actively probing systems across the internet, moving beyond theoretical knowledge into direct observation. The foundation was carefully laid: a dedicated cloud server instance running Ubuntu Live Server, providing an isolated environment specifically for this purpose. The core of this initiative became T-Pot, selected for its ingenious approach to deploying a wide array of honeypot services simultaneously using Docker containers. T-Pot acts as a sophisticated lure, bundling numerous decoy services designed to attract and log interactions from automated scanners and opportunistic attackers. Its composition is diverse, including well-known honeypots like Cowrie, which expertly emulates SSH and Telnet environments to capture login attempts and session interactions; Dionaea, focused on mimicking low-interaction SMB/CIFS protocols often targeted by worms; Honeytrap, designed to dynamically mirror services on commonly scanned ports; and Elasticpot, specifically configured to imitate vulnerable Elasticsearch instances. The suite extends further, potentially incorporating decoys such as Adbhoney for Android Debug Bridge interfaces, Ciscoasa for Cisco firewall vulnerabilities, Conpot for industrial control system protocols, Mailoney for mail server protocols, Redishoneypot for Redis databases, Dicompot for medical imaging protocols (DICOM), specialized web honeypots like Tanner which interacts with web scanners, Honeypy for various protocols, HoneyML for machine learning service emulation, Miniprint for printer protocols, and even SentryPeer for VoIP/SIP analysis. Deploying this sophisticated collection involved configuring the main T-Pot settings file to suit the environment, then executing the platform's installation script, which automates the complex setup of these varied containers and their supporting infrastructure.
The moment T-Pot went live, the reality of internet background radiation became strikingly clear, registering an overwhelming twenty-two thousand connection attempts and probes within the initial 24 hours. This sheer volume immediately highlighted the critical need for efficient data management and analysis capabilities. T-Pot addresses this by seamlessly integrating the Elastic Stack: logs from all the disparate honeypot containers are collected and channelled into Elasticsearch, a powerful search and analytics engine built to handle and index massive streams of time-series data like security logs. This forms the central repository, the memory bank of the entire operation. The primary interface for visualizing and making sense of this data torrent is Kibana, which provides dashboards offering immediate insights into attack volumes, source locations via the compelling Attack Map, targeted services, and common credentials observed across the honeypots.
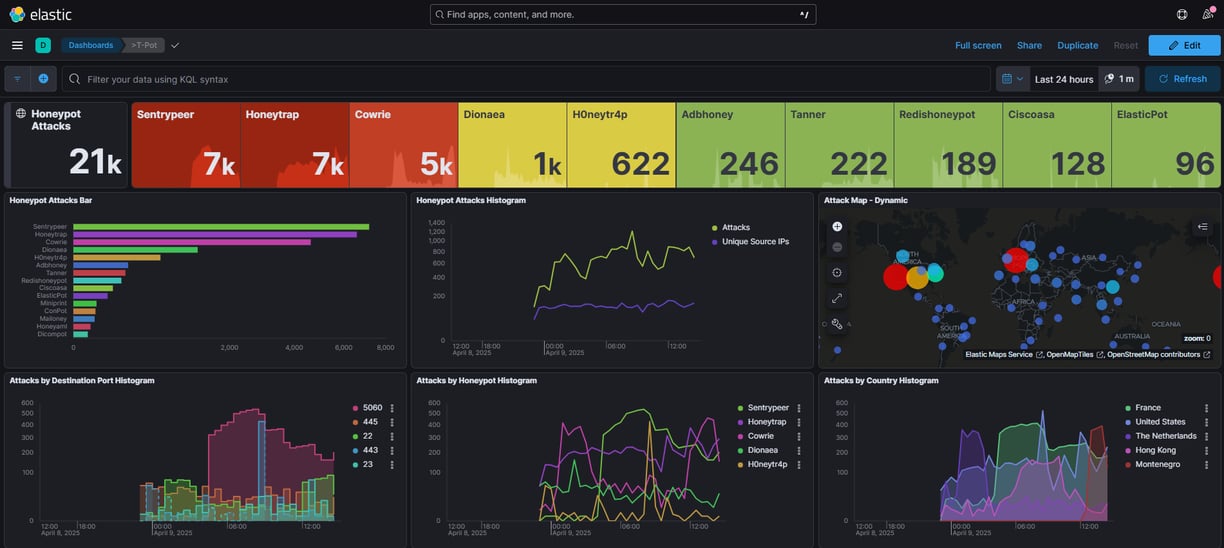


However, understanding the nuances behind those twenty-two thousand hits required diving much deeper than aggregated dashboards. The investigation truly begins by scrutinizing the raw log data captured by T-Pot's sensors and processed through Elasticsearch. A crucial first step involves investigating the source IP addresses recorded for each interaction. Taking these IPs, especially those repeatedly hitting sensitive ports like 3389 (RDP) or those flagged by internal rules as known scanners, and enriching them through external threat intelligence platforms like VirusTotal or AbuseIPDB reveals their reputation and history. Analyzing the provided GeoIP and ASN information (like identifying traffic originating from large data centers such as Vultr or OVH, as initially observed) helps differentiate between potentially compromised servers used for scanning and other sources. Using Kibana itself to correlate activity, searching for single IPs targeting multiple ports or appearing over extended periods, adds further context to the attacker's intent or persistence.
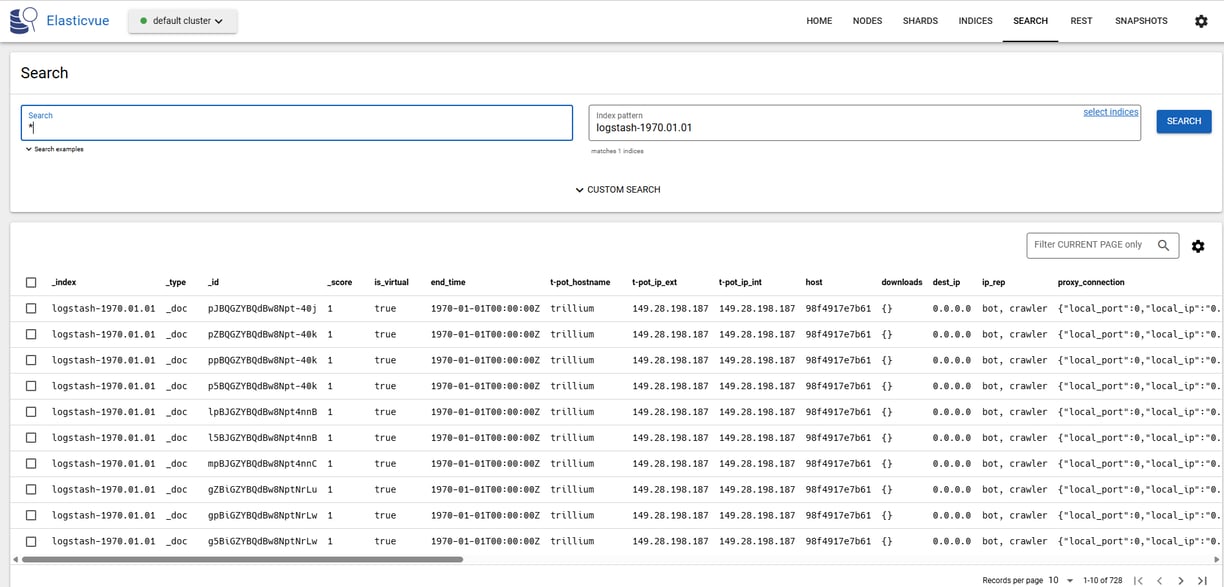
Beyond identifying the source, analyzing the how involves examining the protocols and any available payload data. Logs often contain details like HTTP User-Agent strings, where values like Mozilla/5.0 zgrab/0.x clearly indicate automated scanning activity. Examining requested URLs can reveal attempts to find specific vulnerable files or administration interfaces. While initial connection logs might be limited, deeper inspection, potentially using tools like Elasticvue for direct Elasticsearch queries, or analyzing logs from specific honeypots like Cowrie or Dionaea, can uncover attempted usernames, passwords, executed commands, or even uploaded malware samples. Furthermore, the TLS negotiation process itself leaves valuable clues. TLS fingerprinting, using JA3 and JA3S hashes captured by network sensors like Suricata (often integrated within T-Pot), can help identify specific malware families or scanning tools based on their unique cryptographic negotiation characteristics; looking these hashes up on specialized feeds can instantly classify certain connections.
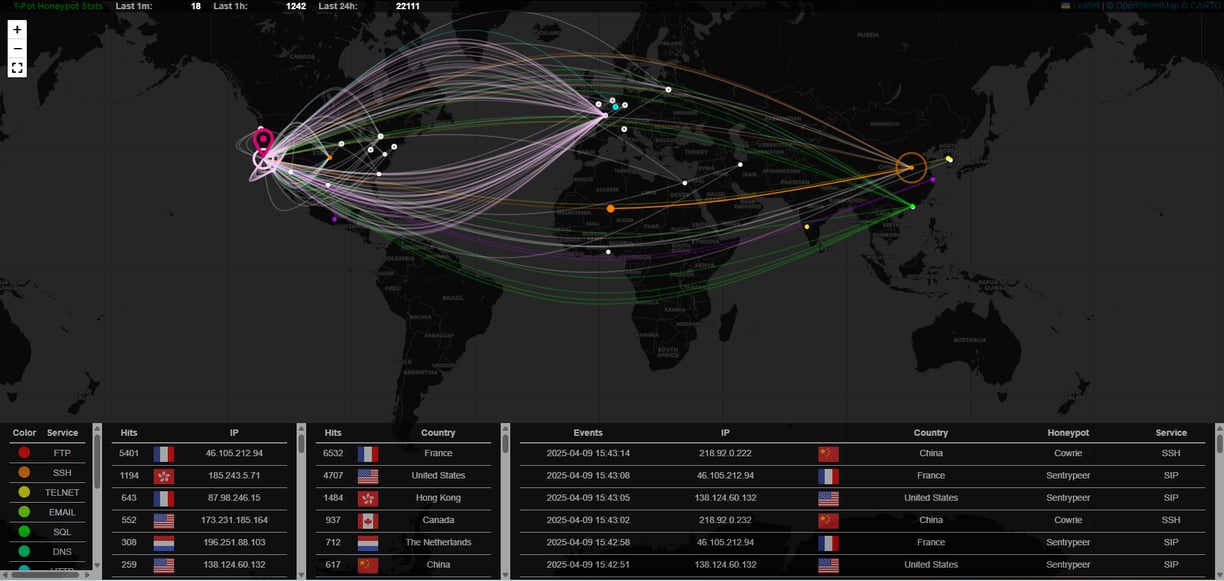
Additional insights come from analyzing the digital fingerprints left by the attackers' tools and operating systems. P0f logs, for instance, attempt to passively fingerprint the OS and network stack based on TCP/IP characteristics, sometimes grouping different IPs that might be using the same toolkit. Suricata, the intrusion detection system often running within T-Pot, generates specific alerts with signatures (like ET SCAN Zmap User-Agent) that provide immediate context about the detected activity; researching these signature IDs offers detailed information about the threat or technique observed. To facilitate the analysis of captured data, especially encoded or obfuscated payloads, T-Pot includes Cyberchef, the invaluable "Cyber Swiss Army Knife," allowing for on-the-fly data manipulation and decoding. Complementing this is Spiderfoot, which automates the process of OSINT gathering, taking identified attacker IPs and enriching them with publicly available information to build a more complete profile. This entire ecosystem, from the diverse honeypot sensors attracting initial contact to the powerful backend storage and analysis tools provided by Elastic, Kibana, and specialized utilities like Cyberchef and Spiderfoot, transforms the raw flood of connections into a rich source of actionable threat intelligence and a profound learning environment. The initial twenty-two thousand hits were not just noise; they were the opening chapter in an ongoing investigation into real-world attack methodologies.
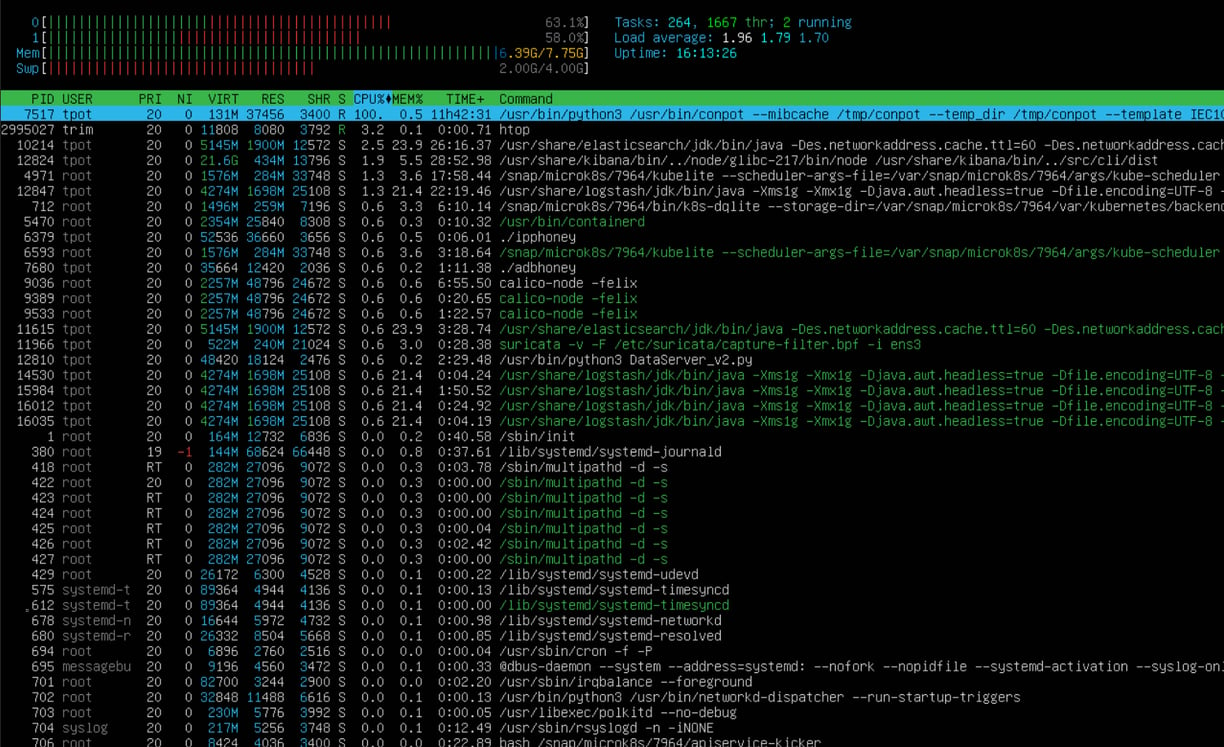
Ultimately, this honeypot deployment transcends a simple technical setup; it functions as a dynamic, real-time observatory positioned directly at the edge, capturing the unfiltered reality of the modern cyber threat landscape. The initial, staggering deluge of twenty-two thousand interactions within the first twenty-four hours served as a stark, immediate illustration of the constant, automated probing that internet-facing systems endure, validating the project's premise and the effectiveness of the T-Pot suite as an attractive lure. However, the true potency of this initiative emerges not just from attracting attacks, but from the synergistic interplay of its carefully chosen components – the diverse array of T-Pot's honeypot sensors acting as the front line, the robust Elastic Stack efficiently ingesting and indexing the resulting torrent of data, Kibana providing the crucial visualization layer with its revealing dashboards and attack maps, and specialized tools like Cyberchef and Spiderfoot enabling deeper analysis of payloads and attacker origins. Yet, maintaining comprehensive situational awareness extends beyond monitoring the honeypot's internal logs and captured interactions. Monitoring the health and performance of the underlying host server itself is equally paramount. Regularly utilizing tools like htop directly on the Ubuntu Live Server provides crucial, real-time visibility into system processes, CPU load, memory usage, and network activity. This ensures the server resources aren't being overwhelmed by the numerous Docker containers managed by T-Pot and helps identify any potential performance bottlenecks or anomalous resource consumption that could indicate issues with the honeypot platform itself, thereby safeguarding the integrity of the entire observation platform.
But the deployment itself, along with the configuration of these powerful tools, is merely the prologue to the main story. The core narrative of this project unfolds through persistent, dedicated observation and analysis – an ongoing commitment rather than a finite task. This commitment translates into a daily ritual: sifting through the data presented in Kibana, investigating anomalies flagged by Suricata or behavioral changes noted in specific honeypot logs, scrutinizing resource trends revealed by htop, and correlating disparate events to piece together larger patterns. It involves actively engaging with the data, using the available tools to pivot from an IP address to its history, from a suspicious payload to its decoded meaning, from a TLS fingerprint to known malicious actors. This continuous immersion allows for the recognition of subtle patterns, the identification of emerging campaigns targeting specific vulnerabilities, understanding the sheer relentless persistence of automated credential stuffing attacks, and learning to differentiate the background noise from potentially more targeted reconnaissance. It's the profound difference between reading a static threat report and standing directly in the digital weather, observing the shifts in wind direction and intensity firsthand. This sustained vigilance cultivates a deeper, more intuitive grasp of attacker Tactics, Techniques, and Procedures (TTPs) and the ever-evolving threat landscape, fueling the development of not just reactive defenses, but proactive, threat-informed security thinking grounded in practical, hard-won experience.